Understanding Bizzkit User Management
Bizzkit User Management is a powerful solution that enables effective management of users and access within a Bizzkit online store solution. Comprising two core applications, 'AUTH' for user authentication and 'IAM' for user and role management, the system is critical for protecting both UI applications and API, as well as facilitating communication between internal and external applications.
In this article, we will explore the foundational features and terminology of Bizzkit User Management, providing you with a understanding of how it can streamline user management and enhance security in your e-commerce environment.
Key features of Bizzkit User Management includes:
- Robust and secure authentication and authorization
- Complies with OAuth 2.0 and OpenID Connect standards
- Offers a user interface for managing users, roles, and their relationships
- Features a customizable login user interface
- Can connect to other oauth providers like Microsoft, Google, Auth0, etc.
- Provide a way to use a local login feature with MFA
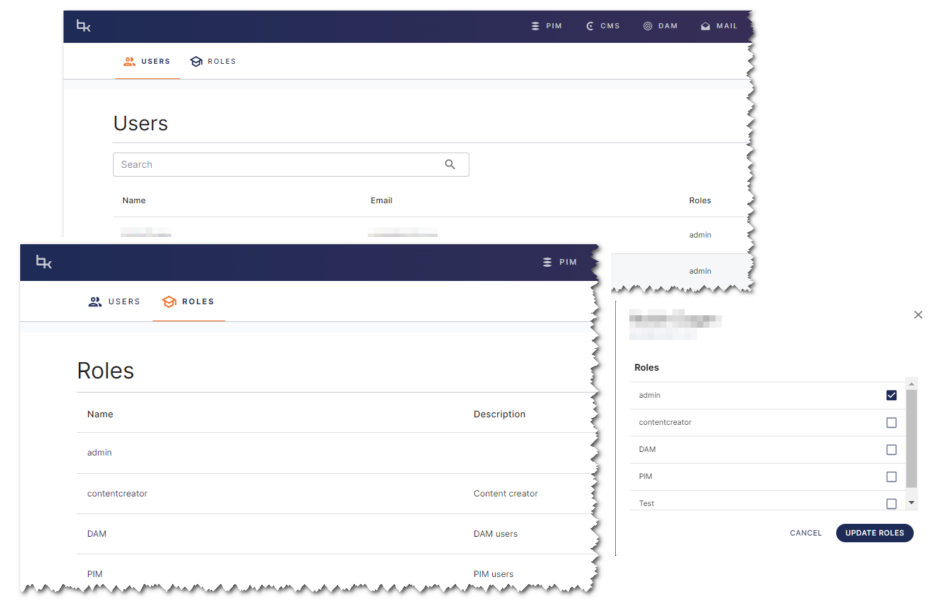
Users and roles
In Bizzkit User Management, a user is the representation of a person who can access one or more protected resources. For example, Alice is a user who may need access to the Bizzkit platform or other resources protected by the system.
A role, on the other hand, is the function or set of functions that a user has in the system. A user can have one or more roles assigned to them in order to access the resources they need. For instance, Alice may be a system administrator who needs to manage other users and resources, as well as a publisher who needs to add and edit content in the CMS.
Bizzkit User Management offers an easy-to-use interface for managing users and roles. With this interface, administrators can add, edit, or remove users as needed, as well as assign and manage roles for each user. This makes it simple to ensure that each user has the appropriate access and permissions to perform their assigned tasks.
It's important to note that permissions for specific applications, such as the Product Information Management (PIM) or Digital Asset Management (DAM), are handled within those applications themselves. Bizzkit User Management provides a centralized location for managing users and roles, but the permissions for specific resources are managed within their respective applications.
Practical example
After installing the Bizzkit platform, Alice, the IT administrator, is now ready to give her colleague Bob access to Bizzkit DAM. In their company, all users are already created in the Microsoft Office 365 account used for company emails and other purposes. To add Bob to the system, Alice adds the company's Office 365 account to the list of upstream providers in the IAM.
Next, Alice adds Bob to the list of users and assigns him to a new role called "marketing-assistant" in the IAM. This new role is reflected in Bob's user profile the next time he logs in, but since it is a new role, it doesn't have any permissions assigned yet. Alice logs into the CMS to define what tasks a "marketing assistant" is allowed to perform.
Bob can now access the CMS by visiting the login page, where he is redirected to the Office 365 account to verify that he wants to access the Bizzkit platform. After confirming his credentials, he is redirected back to the CMS where he can perform the tasks he needs to.
Providers, clients and scopes
Bizzkit User Management uses OpenID Connect (OIDC) to manage authentication and authorization for users. OIDC relies on the use of trusted identity providers, or "upstream providers", to authenticate users and issue ID tokens that can be used to access protected resources.
An upstream provider is an OIDC provider that is trusted by the AUTH component of Bizzkit User Management to authenticate users. AUTH supports multiple upstream providers, and users from different upstream providers are correlated based on email address. Examples of upstream providers that can be used with Bizzkit User Management include AzureAD, Google, and Auth0. These providers can be configured to authenticate users and issue ID tokens that can be used to access protected resources.
In addition to these external providers, Bizzkit User Management also includes its own local provider, allowing users to log in using an email and password combination with additional Multi-Factor Authentication (MFA) protection if required. This local provider can be useful in cases where external providers are not available or desirable.
However, please note that using the local provider is not recommended in production environments, as it may not offer the same level of security and reliability as external providers. Always consider using an external provider for authentication in your production environment to ensure optimal security.
A downstream client is an application that uses AUTH to authenticate its users or authenticate itself when calling APIs. AUTH supports different types of downstream clients:
- Machine applications are systems that act on their own behalf when interacting with a protected API.
- Interactive applications are server-side clients that use AUTH to authenticate their users, such as a web application.
- Client-side applications are untrusted applications that authenticate on behalf of the user before accessing a protected API, such as a React app.
- A protected API is an API that is protected by AUTH.
A scope is a sub-part of a protected API that represents a specific set of permissions that a user or client has for accessing that API. In Bizzkit User Management, a scope is a simplified version of the concept of an "API Scope" in IdentityServer. By using scopes, administrators can ensure that users and clients have access only to the specific resources and permissions they need to perform their tasks, while also improving the security and reliability of the system.
About OAuth 2.0 and OpenID Connect
OAuth 2.0 is an authorization framework that enables applications to obtain limited access to a user's protected resources. It simplifies the process of securing APIs and provides multiple authentication flows for different use cases. OpenID Connect is an identity layer built on top of OAuth 2.0. It enables clients to verify a user's identity based on the authentication performed by an authorization server. OpenID Connect also provides basic profile information about the user.
Bizzkit AI assistant
The Bizzkit AI Assistant (BAIA) is an advanced optional feature within the Bizzkit platform, designed to enhance user experience through automation and intelligent interaction. It serves several purposes:
- BAIA is based on the latest AI models, allowing users to interact with it using natural language.
- BAIA possesses comprehensive and updated knowledge of Bizzkit documentation and can, therefore, provide users with answers to questions about all products and features.
- BAIA can access the Bizzkit APIs, enabling users to communicate with it in natural language to both query and modify data across different products. Leveraging its language model foundation, BAIA can also enrich queries with additional data.
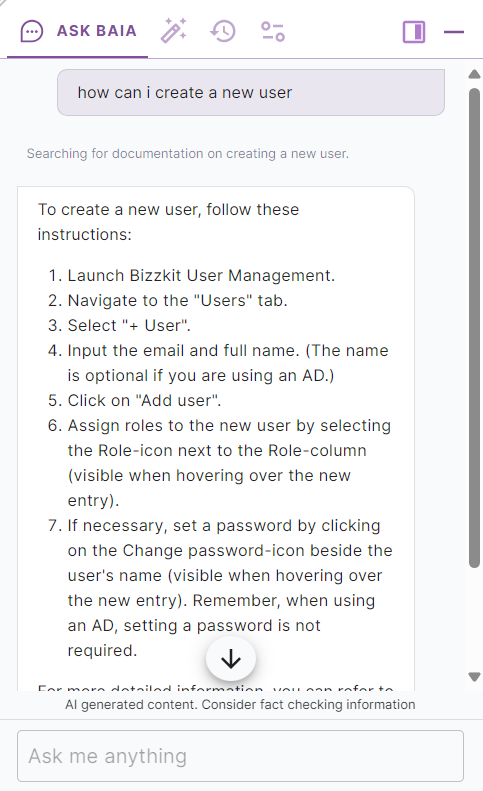
In user management, using BAIA makes it extremely easy to access documentation in a natural way. Here is an example of how to create a new user:
Using BAIA to access the API can also be extremely effective and time-saving. Here is a video showing how to use a system recipe to export users in a specific group to different formats.